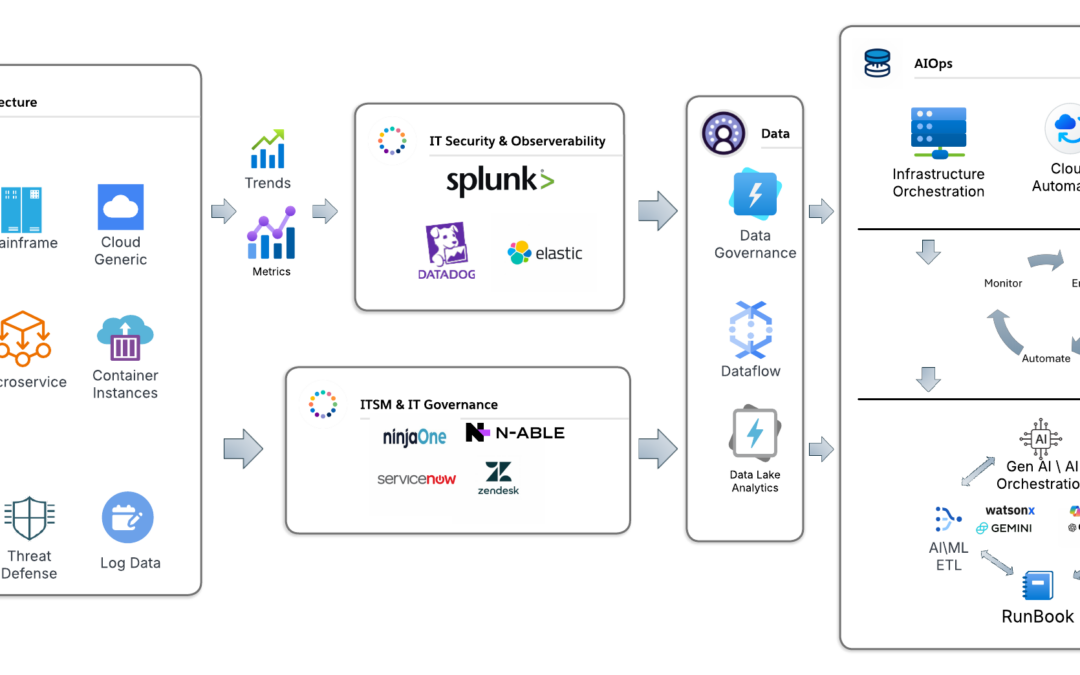
Apr 3, 2025 | Uncategorized
In today’s digital-first environment, IT systems are more complex than ever. Between hybrid infrastructure, legacy applications, microservices, and growing security demands, operations teams are being pushed to their limits. That’s where AIOps—Artificial Intelligence...

Dec 31, 2024 | Uncategorized
[ALEXANDRIA, VA, UNITED STATES, December 18, 2024] – End to End Enterprise Solutions (E3S), a leading provider of AI-powered autonomous systems and Cybersecurity solutions, and BizzTech, an AI powered Metaverse platform, are proud to announce a strategic partnership...

Oct 21, 2024 | Uncategorized
At End to End Enterprise Solutions, we are specialists in Cybersecurity and AI development and services; we believe we have a duty to fully synchronize the two disciplines as we plan and secure our clients’ cyber posture so that the actions are more efficient and...

Sep 24, 2024 | Autonomous Operations, Cloud Security, Cybersecurity, Uncategorized
According to Deloitte, their “2023 Deloitte and Manufacturing Leadership Council (MLC) Industrial Metaverse Study reveals that manufacturers have an opportunity to build on their smart factory momentum to springboard into the industrial metaverse.” Article 3 September...
Mar 28, 2024 | Advanced Tech, AI-ML, News Feed, Uncategorized
E3S joined NASA Stennis Space Center, and Sidus Space, in celebrating the deployment of NASA Stennis’ first-ever in-space autonomous systems mission. Successfully developing the autonomous software for the Sidus LizzieSat-1™ is monumental, and speaks volumes about the...

Nov 23, 2020 | Articles, Business Transformation, Cloud Security, Compliance, Cybersecurity, Innovation, Uncategorized
Securing your organization’s network has become an increasingly critical task each year. As many operations are becoming virtual, the responsibility and sophistication of IT networks has seen rapid growth. With this virtualization comes an increased reliance on IT...